AWS Control Tower with CDK: set up IAM Identity Center
Table of Contents
When setting up access to your AWS accounts governed by AWS Control Tower, you have two options:
- Allow Control Tower to configure account access with IAM Identity Center.
- Configure IAM Identity Center or another access method yourself.
If you decide to let Control Tower manage account access with IAM Identity Center, the setup process can be straightforward or complex, depending on your Control Tower configuration. For instance, using CDK can make the process less smooth.
In this article, we’ll explore how to properly set up AWS account access with IAM Identity Center when deploying the Landing Zone via CDK.
In case you’re unfamiliar, AWS Control Tower is a service that simplifies the provisioning, setup, and governance of a secure, multi-account AWS environment, known as a Landing Zone. For more information, consult the Control Tower User Guide.
IAM Identity Center configuration using the console #
As shown in the image below, configuring IAM Identity Center through the console is as simple as selecting an option. AWS Control Tower will handle:
- Enabling IAM Identity Center if it isn’t already enabled.
- Creating a preconfigured directory with user groups and permission sets.
- Setting up essential user groups and permission sets.
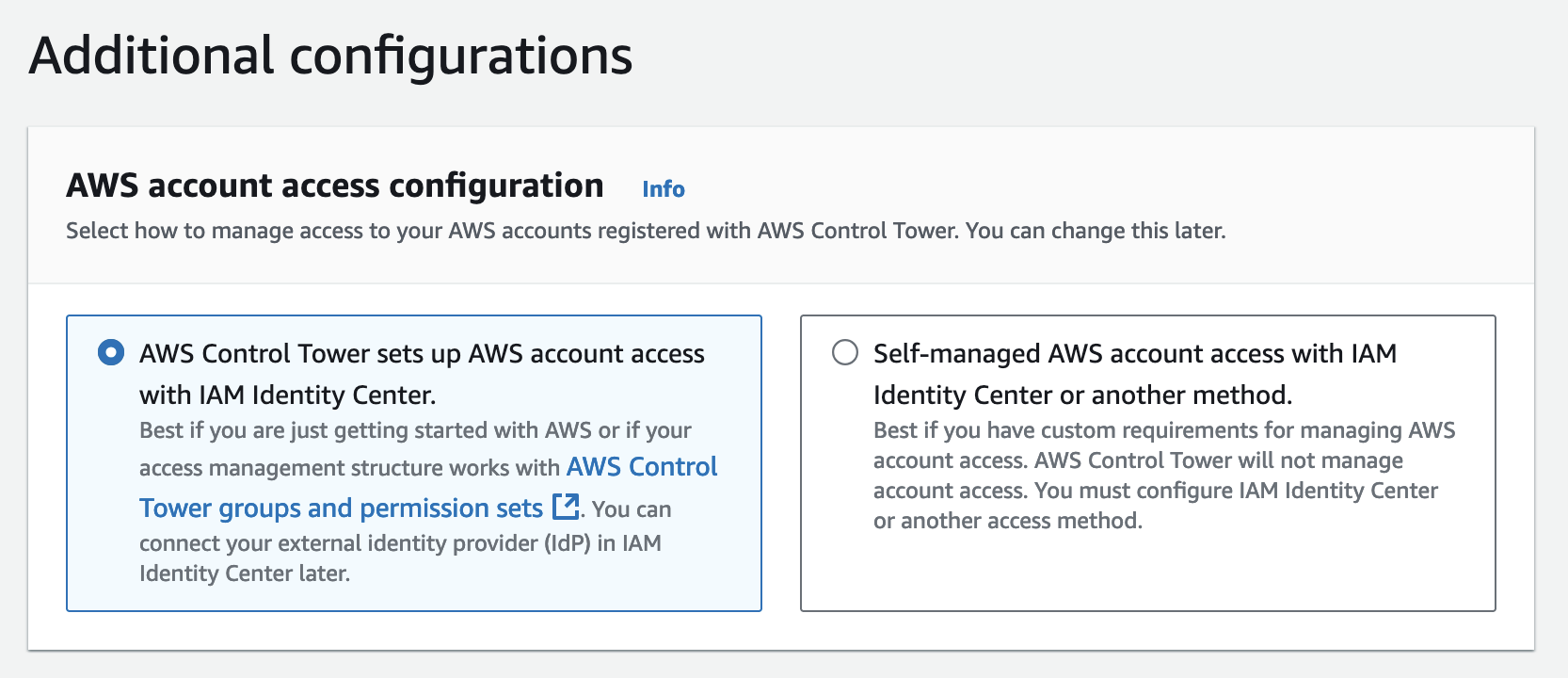
Naturally, I expected the same streamlined experience with CDK—but this wasn’t exactly the case.
IAM Identity Center Configuration When Deploying Control Tower with CDK #
First of all, CDK currently lacks an L2 construct for Control Tower ( AWS CDK documentation). This means you’ll need to use an L1 construct instead. If you’re unfamiliar with CDK constructs, refer to the constructs documentation.
Basically, L1 constructs map directly to individual AWS CloudFormation resources, so you’ll need to reference CloudFormation resources and configure properties accordingly.
Let’s review the Control Tower Landing Zone CloudFormation reference:
Type: AWS::ControlTower::LandingZone
Properties:
Manifest:
Tags:
- Tag
Version: String
Among the properites, Manifest and Version are required. The Manifest property specifies the Landing Zone configuration, but there’s little documentation explaining the necessary configurations for it. 💔
To be honest, I had a hard time finding clear documentation on the manifest file. This page was all I found, but it lacks a detailed explanation of each property. For instance, it’s not immediately clear that the accessManagement.enable property enables IAM Identity Center.
Below is an example of the Landing Zone CDK resource configuration:
const landingZone = new CfnLandingZone(this, 'LandingZone', {
manifest: {
...
accessManagement: {
enabled: true
}
...
},
version: '3.3'
})
Setting accessManagement.enable to true instructs Control Tower to create the user groups and permission sets, but it doesn’t actually enable IAM Identity Center. This resulted in the following error:
Error AWS Control Tower failed to set up your landing zone completely:
The management account does not contain an IAM Identity Center directory.
This means I needed to enable IAM Identity Center first.
Enabling IAM Identity Center #
Since I was using CDK, my initial approach was to create an IAM Identity Center instance in my CDK stack. However, I had to abandon this idea quickly.
The
documentation for AWS::SSO::Instance states that you can only create an instance for a standalone AWS account that isn’t managed by AWS Organizations or a member account within an organization—clearly, not my case.
I looked for alternative ways to enable IAM Identity Center without using the console, as I wanted to avoid manual steps, but had no luck. According to the documentation here:
To enable IAM Identity Center, you must sign in to the AWS Management Console
as a user with administrative credentials in your AWS Organizations management account.
Thus, it appears the console is the only option.
To enable it, go to the IAM Identity Center dashboard and click on Enable. It only takes a few seconds.
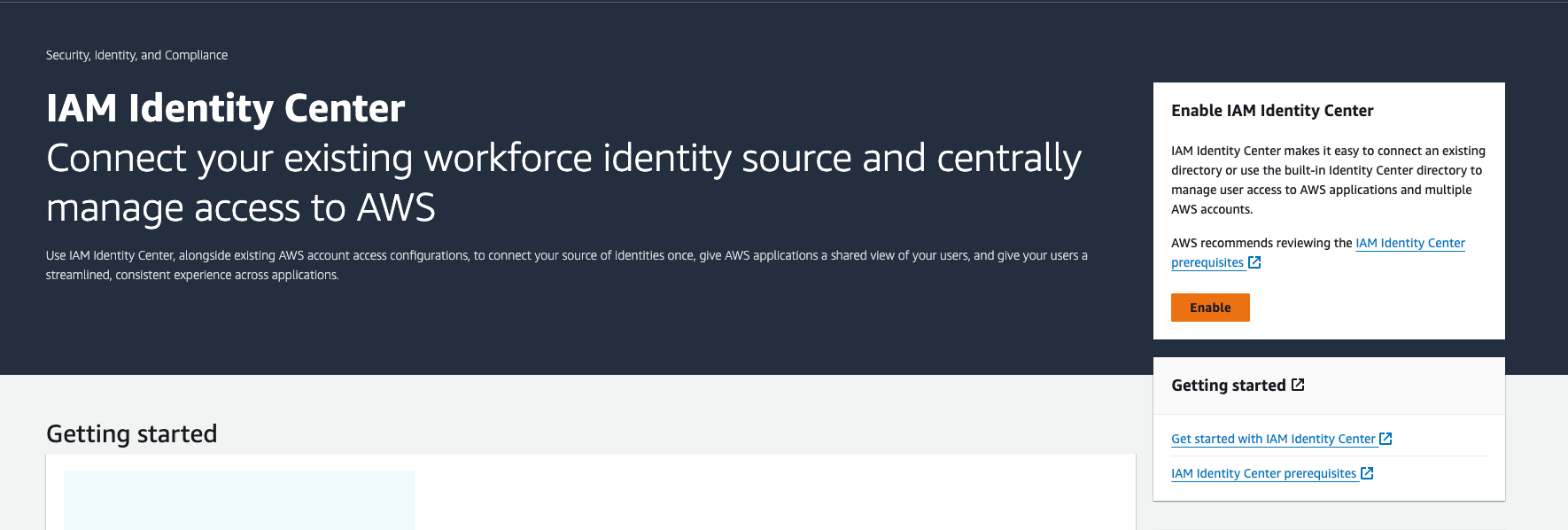
Now that IAM Identity Center is enabled, I could proceed with deploying Control Tower.
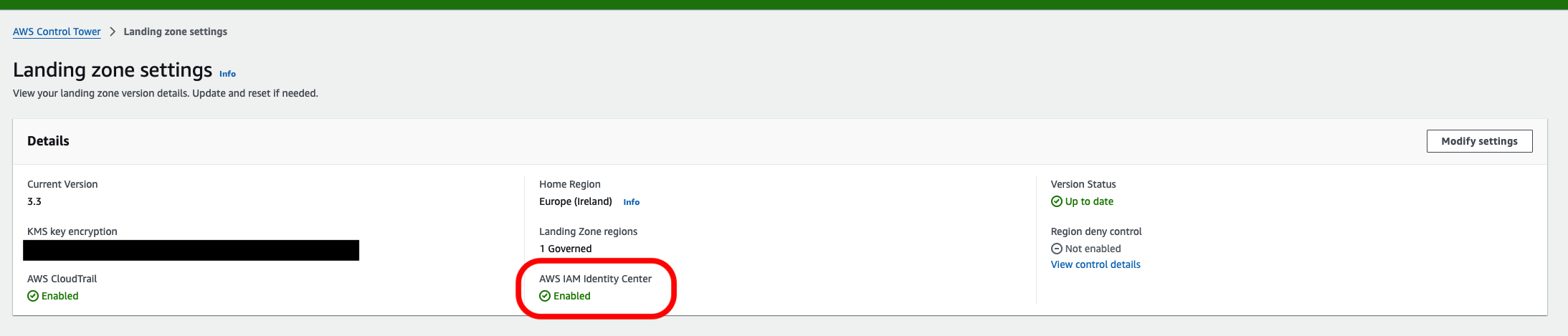
The deployment succeeded, and I confirmed that IAM Identity Center was enabled in the Landing Zone settings.
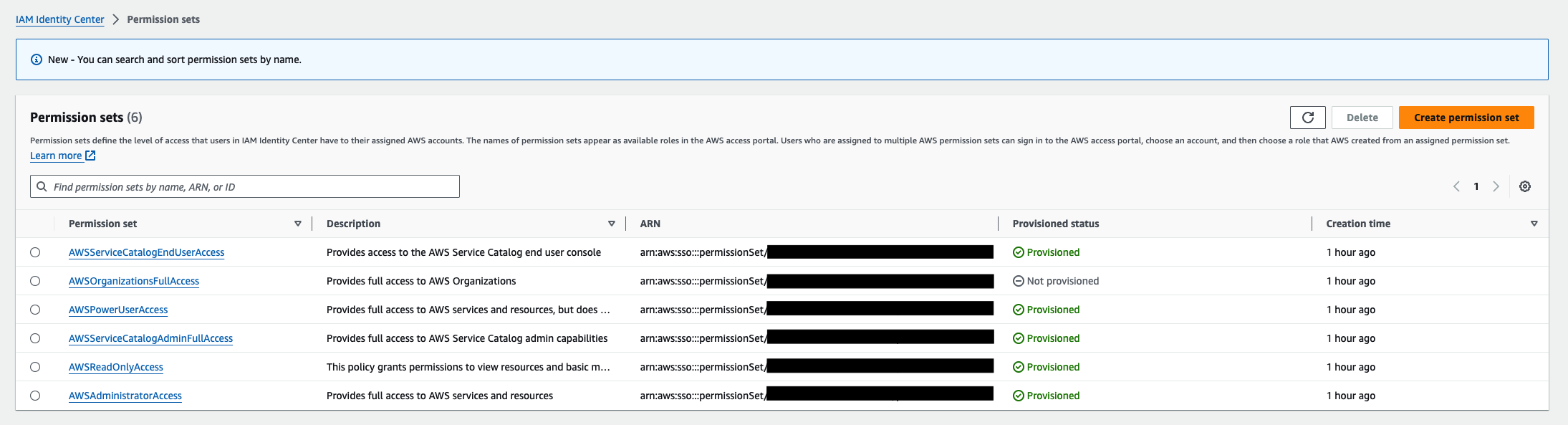
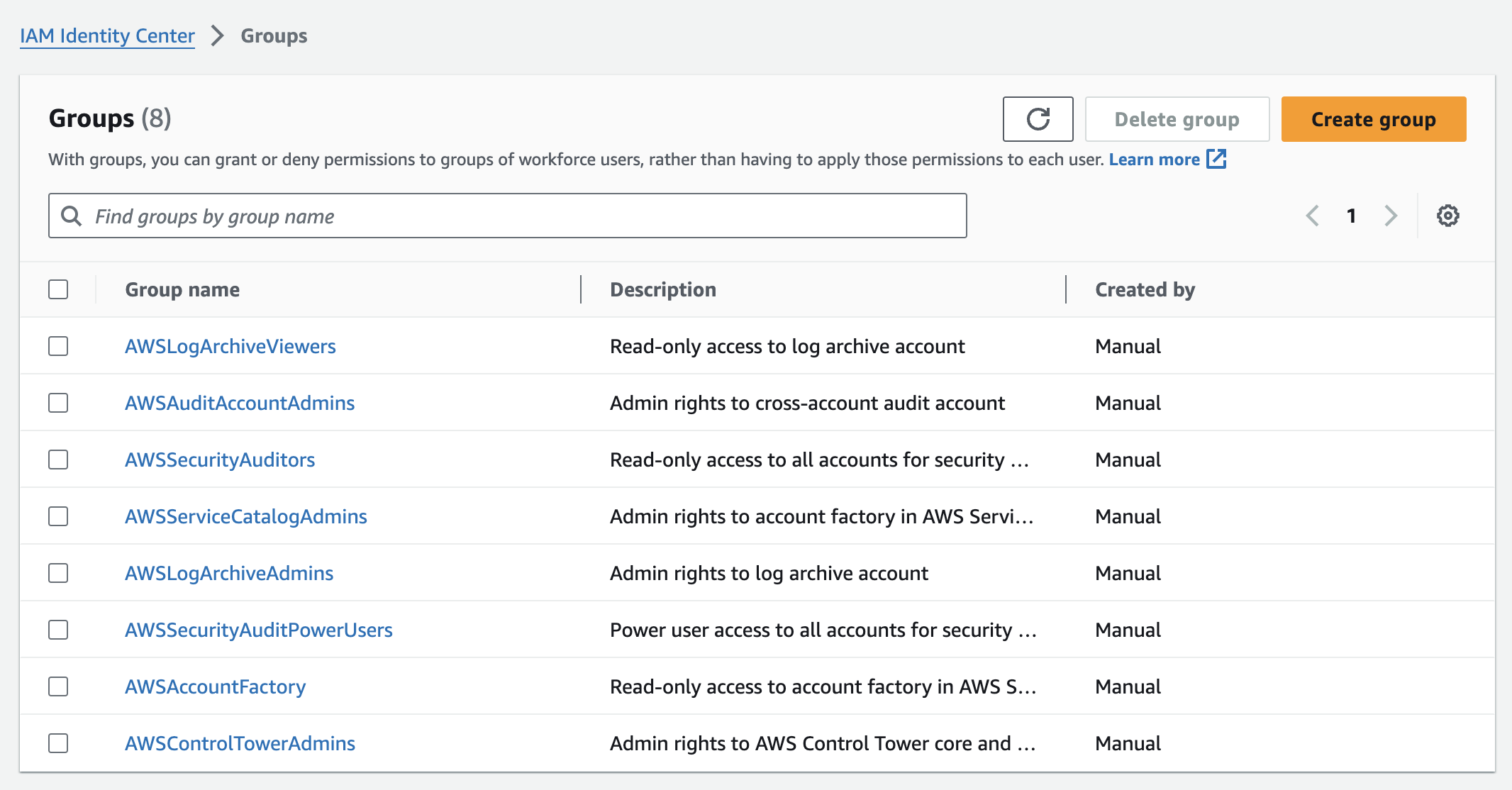
Returning to the IAM Identity Center dashboard, I saw that Control Tower created:
- The AWS Control Tower Admin user.
- 8 user groups.
- 6 permission sets.
Conclusion #
Automating Control Tower deployment is convenient but presents some integration challenges with IAM Identity Center. Today, we reviewed ways to address these limitations.
If you have feedback or alternate solutions, please reach out via email or LinkedIn.
That’s all folks, stay tuned! 🚀
